Last week, the Spectre V2 vulnerability, also known as Branch History Injection, or BHI, was discovered in Intel and Arm processors. Although the Spectre attack has been around for a while, this new line of defence has had a substantial impact on both chip manufacturers.
AMD’s CPUs have a very different design, which has allowed them to avoid injury this week. However, three Intel security researchers recently published a white paper describing code vulnerabilities in AMD’s chipset. In conclusion, AMD has published a new security bulletin to reflect the improved efficiency of their product’s security.
The first Spectre and Meltdown weaknesses were identified in December 2017 and revealed flaws in Intel’s chip designs, which were uncovered by four different research teams and disclosed to the leading firm around the same time. Intel’s plans exposed a weakness in which proof-of-concept code could be injected into the kernel of a computer, allowing access to information that should not be available. The Intel chips had a vulnerability that was discovered in 1993.
When the initial attack findings were discovered, Spectre and Meltdown attacked Intel, Arm, and AMD chips at the same time. Security safeguards were put in place for the chip giants after the initial attacks were mitigated. Nonetheless, they were discovered to be a rapid fix for an issue that would otherwise take years to fix.
The BHI has surfaced in the previous few weeks, reopening the Spectre exploit. The most substantial vulnerability effects were Intel and Arm, according to reports. AMD representatives, on the other hand, claimed that the initial modifications from several years ago were still active in their chipset and that the business could prevent the attack—or so it was assumed.
The AMD strategy for Spectre V2 mitigation, based on the Retpoline strategy, as detailed by the VUSec group at Vrije Universiteit Amsterdam. The research team notes that AMD’s LFENCE/JMP-based Retpoline code is deemed insufficient in their findings. AMD claims that the approach it uses works better on its technology than “generic” Retpoline codes, which they claim “result in a RET on indirect branches.” The default process redirects indirect branches to the LFENCE/JMP, protecting AMD’s chipset from Spectre V2 attacks.
While AMD’s chips are not directly affected by the Spectre BHB/BHI vulnerabilities, the firm was made aware of the approach used to handle the vulnerability, which has caused more problems for AMD’s Zen-based processors. To effectively manage the Spectre V2 exploit, the organisation is now implementing the recommended “generic” Retpoline approach.
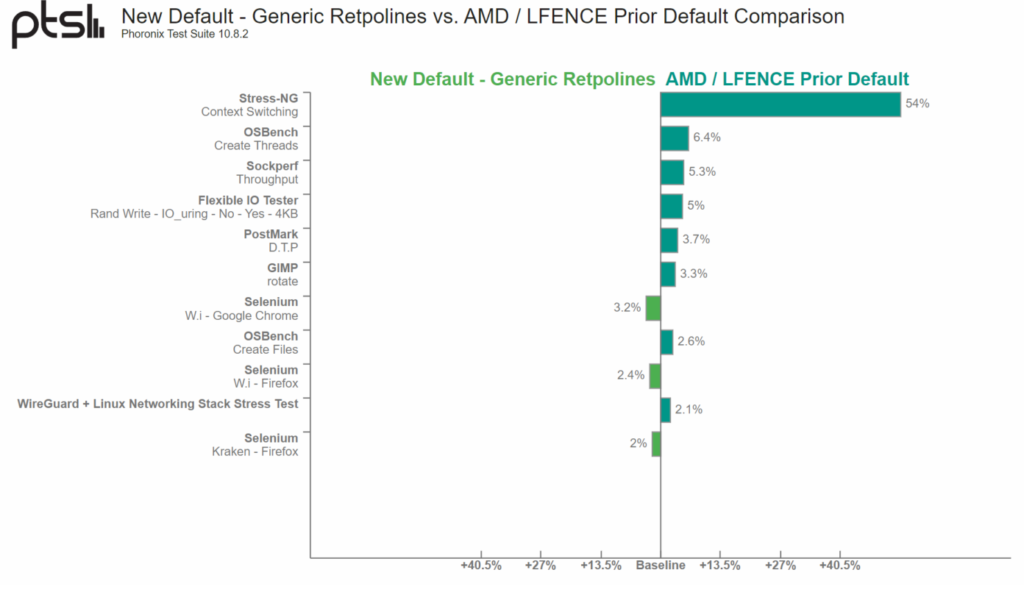
AMD retpoline may be susceptible to speculation. The speculation execution window for an incorrect indirect branch prediction using LFENCE/JMP sequence may potentially be large enough to allow exploitation using Spectre V2. By default, don’t use retpoline, fence on AMD. Instead, use the generic retpoline. — AMD
The team from Intel’s IPAS STORM, which includes Ke Sun, Alyssa Milburn, Henrique Kawakami, Emma Benoit, Igor Chervatyuk, Lisa Aichele, and Thais Moreira Hamasaki, is mentioned in AMD’s security bulletin. Milburn, Sun, and Kawakami’s paper, “You Cannot Always Win the Race: Analyzing the LFENCE/JMP Mitigation for Branch Target Injection,” expands on AMD’s problem and updates prior studies with new material discovered and submitted to AMD.
LFENCE/JMP is an existing software mitigation option for Branch Target Injection (BTI) and similar transient execution attacks stemming from indirect branch predictions, which is commonly used on AMD processors. However, the effectiveness of this mitigation can be compromised by the inherent race condition between the speculative execution of the predicted target and the architectural resolution of the intended target, since this can create a window in which code can still be transiently executed. This work investigates the potential sources of latency that may contribute to such a speculation window. We show that an attacker can “win the race”, and thus that this window can still be sufficient to allow exploitation of BTI-style attacks on a variety of different x86 CPUs, despite the presence of the LFENCE/JMP mitigation.
While it may appear like Intel wants to smear AMD’s reputation to gain market share, this is far from the case. The team examines potential security concerns, according to Intel. Assume their product or the products of any other company faces a danger of this scale. In that scenario, it’s better to cooperate and collaborate to reduce such large threats, so that everyone benefits from any risks.
Also Read: