In a January update, AMD quietly disclosed 31 new CPU vulnerabilities spanning its Ryzen consumer chips and EPYC data centre processors. The vulnerability update also includes a list of AGESA versions, as well as mitigations for affected processors. AMD disclosed the flaws in a coordinated disclosure with several researchers, including teams from Google, Apple, and Oracle, giving the company time to develop mitigations before the public listings.
The interesting thing here is that AMD did not announce the vulnerabilities through a press release or other means, instead simply posting the lists. The list includes AGESA revisions that AMD has distributed to its OEMs in order to patch the vulnerabilities (AGESA code is used to build BIOS/UEFI code). The availability of new BIOS patches with the new AGESA code, on the other hand, will vary by vendor.
So its better if you with your motherboard or system vendor to see if new BIOS revisions with the correct AGESA code have been posted.
AMD says it typically releases vulnerability disclosures twice a year, in May and November, but chose to release some in January due to the relatively large number of new vulnerabilities and the timing of the mitigations. It is unclear whether there will be performance penalties, as with other mitigations such as Spectre and Meltdown.
Three new variants of the vulnerabilities affect the consumer-oriented Ryzen desktop PC, HEDT, Pro, and Mobile processors. One vulnerability is classified as high severity, while the other two are classified as medium or low severity.
These flaws can be exploited via BIOS hacks or an attack on the AMD Secure Processor (ASP) bootloader.
The flaws affect the Ryzen 2000-series Pinnacle Ridge desktop chips, as well as the 2000- and 5000-series APU product lines with integrated graphics (Raven Ridge, Cezanne). Furthermore, AMD’s Threadripper 2000- and 3000-series HEDT and Pro processors, as well as numerous Ryzen 2000-, 3000-, 5000-, 6000-, and Athlon 3000-series mobile processors, are affected.
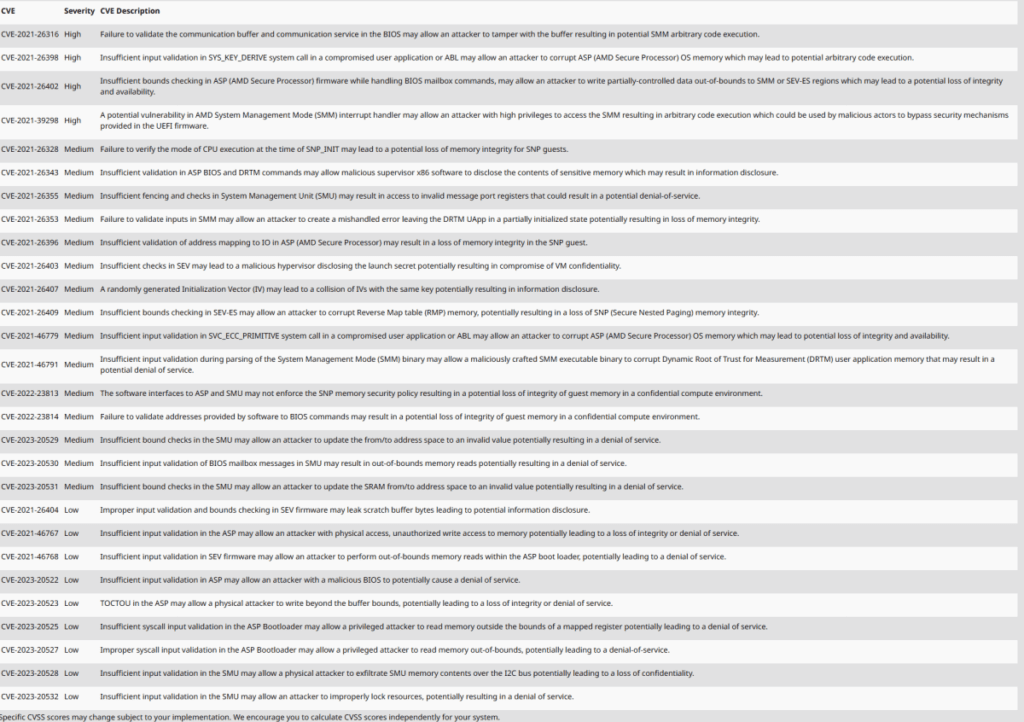
AMD has also disclosed 28 EPYC processor vulnerabilities, four of which are of high severity. Three of the high-severity variants allow arbitrary code execution via various attack vectors, while another allows writing data to specific regions, which can result in data integrity and availability loss. Researchers also discovered 15 other medium-severity vulnerabilities and nine low-severity vulnerabilities.
Also Read:








