The idea that a quantum computer could one day destabilise bitcoin is gaining traction. Because quantum computers are becoming strong enough to factor big prime numbers, a vital component of bitcoin’s public-key cryptography, this is the case.
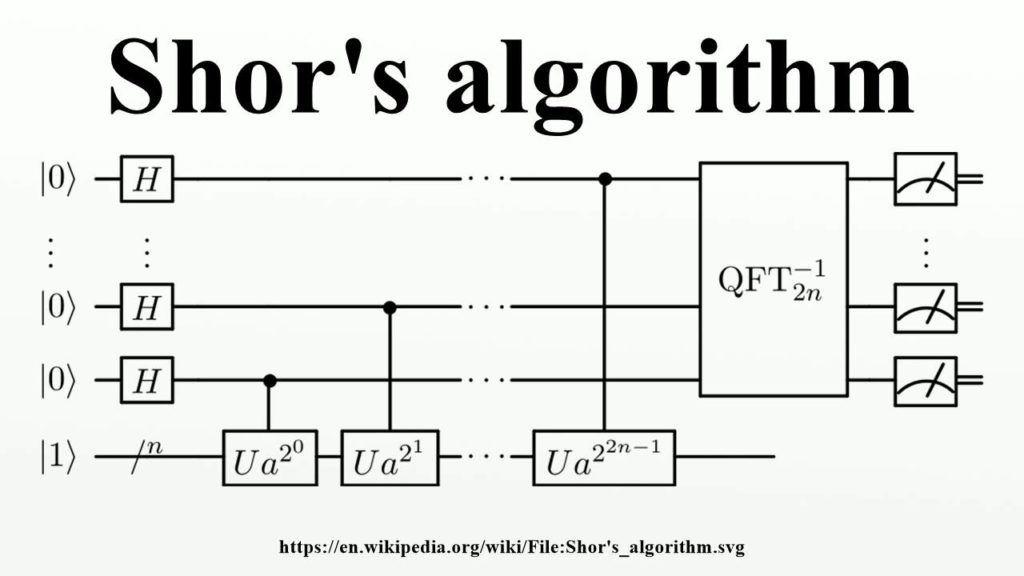
This accomplishment is accomplished by quantum computers using Shor’s algorithm. Shor’s approach reduces the time it takes to tackle factorization issues considerably. It’s also made for quantum computing since it takes advantage of quantum computing’s “superposition” of states.
Untangling the Mysteries of Public Key Cryptography:
Public-key cryptography underpins the security of wallet creation and transaction signature. What is public-key cryptography, and what are its advantages and disadvantages?
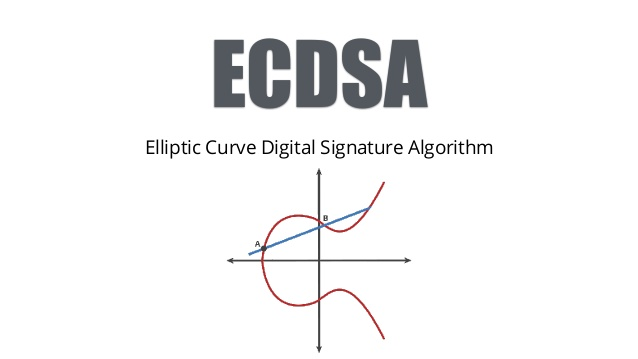
To begin, an Elliptic Curve Digital Signature Algorithm (ECDSA) is used to generate a private key and its corresponding public key in Bitcoin’s protocol. Both are important for Bitcoin users to understand.
To generate your bitcoin’s public address, you’ll need to use a hash function (what you send and receive funds with). This public key was created with the intention of being shared with other users. The fact that crypto users feel forced to keep their public key hidden implies that the key system is defective from the start.
Private keys are kept secret because they are used to sign and validate transactions.
While a user’s public key can be calculated using his or her private key, private keys cannot be calculated using public keys. This “one-way function” is based on the fact that no traditional computer can factor huge prime integers easily.
Shor’s Algorithm and Its Magic:
Peter Shor, a mathematician, demonstrated in 1994 that a quantum algorithm can generate a private key from a public key. Shor’s algorithm does this by lowering the number of steps needed to determine prime factors of huge numbers.
A traditional computer can reduce every factor problem to an order-finding problem, but it cannot solve the order-finding problem. Quantum computers, on the other hand, are incredibly good at finding orders. This is due to the exponential scaling of their speedup over traditional techniques.
Anyone with a powerful enough quantum computer (approximately 2300 qubits) may reconstruct a private key from its corresponding public key using Shor’s technique.
An attacker can produce a digital signature that can be verified by the appropriate public key once a private key is known. This allows an attacker to gain access to a user’s account funds, as you might expect. The attacker may be able to obtain further information about the user depending on the account. Identity theft becomes a distinct possibility in this situation.

Finding Vulnerable Individuals:
A user’s public key was their receiving address in the early days of Bitcoin. As a result, anyone making a bitcoin transaction may see the recipient’s public key easily.
Experts in cryptography quickly noticed that these p2pk (pay to a public key) addresses could be attacked in the future. ‘Pay to pubkey hash’ (p2pkh) addresses began replacing p2pk addresses in 2010. (still used today).
Reused p2pkh addresses, by the way, should also be avoided. A person’s public key becomes public after they send funds from a p2pkh address. As a result, many wallets now make it impossible to reuse an address.
In total, these two sorts of addresses own around a fifth of all bitcoins (p2pk and reused p2pkh). Anyone with a strong quantum computer may calculate the private key from such an address, making these coins extremely vulnerable to theft.
Despite the fact that the majority of bitcoin investors no longer utilise p2pk addresses, they are still vulnerable. Bitcoin’s price will almost certainly plummet once a quantum computer publicly generates a private key from a public key.

Hijacking a Transaction:
An attacker who can hijack a (live) transaction must complete a number of activities quickly. The attacker must then generate, sign, and publish the conflicting transaction after using Shor’s method to derive the private key.
If you have a powerful quantum computer, you can do all of these procedures quickly. With the exception that the attacker is the lone benefit, the result will be comparable to a double-spending attack.
This transaction hijacking attack can be combined with a selfish mining assault by an astute miner. A miner might establish their own secret chain and selectively publish blocks to the public chain with enough quantum computing power.
The quantum attacker will trigger a restructuring of the public chain as a result of this (a rolling back of the chain). In this case, the attacker obtains all cash and block rewards included in any transactions that have been spent — in the transactions that have been altered.
Public Key Visibility and Taproot:
Companies like Glassnode and Chain Analysis may impede Bitcoin users from looking to keep their transactions private. These firms examine the public keys for each transaction as they access and generate the logs from a node’s mempool.
In any case, public keys may be made public again in the near future. Taproot, a bitcoin update, attempts to make all public keys viewable on the blockchain. The goal of this improvement is to improve the flexibility of bitcoin transactions (such as enabling the use of new signature types).
The taproot will, of course, increase bitcoin’s quantum vulnerability by making public keys exposed. Critics argue that such an upgrade is unnecessary because bitcoin is primarily used as a store of currency.

There Are No Simple Answers:
Given these difficulties, it appears reasonable to require that all bitcoins be transferred to a new p2pkh address. Aside from the potential legal ramifications, it’s unlikely to be a long-term solution.
Quantum computers will soon be fast enough to circumvent p2pkh safeguards. Instead, it appears that implementing quantum-resistant cryptography is the most plausible solution to this problem.
In this procedure, the Quantum Resistant Ledger (QRL) is crucial. XMSS is a quantum-resistant hash-based signature technique included in the cryptocurrency (eXtended Merkle Signature Scheme). QRL can also upgrade this signature scheme if necessary without jeopardising its security.
However, QRL did not just establish a solo post-quantum blockchain. It also invented enQlave, an ethereum wallet that prevents quantum theft of any ether or erc20 token balance. On ethereum, this innovation uses XMSS signature verification.
After determining that quantum computers are a fatal danger to cryptocurrencies, Peter Waterland founded QRL.

Final Words:
It’s a bit of a gamble to try to solve these issues before quantum computers come. It’s the equivalent of repairing a car engine while it’s rolling downhill. If you don’t complete in time at the bottom of the hill, the automobile will crash into a cliff. Taproot is like having both the throttle and the brakes open at the same time.
Bitcoin investors who believe quantum computing is still a long way off risk being caught off guard.
Quantum computing has progressed at a breakneck pace, far quicker than many scientists anticipated. Nothing can be taken for granted, especially when tech corporations continue to invest millions of dollars in R&D.
Solutions that use post-quantum cryptography appear to be the best long-term chance for cryptocurrency investors interested in taking a proactive approach to blockchain security.
Quantum Resistant Ledger is now the only blockchain business heading in this approach with credibility. Join us in our Discord channel today for a debate about the future of post-quantum cryptography.
Also Read: